
How does Shush Sherlock work?
Silent Authentication redefines Mobile Security
When traditional user verification (old way) is not enough, enterprise companies turn to Silent Authentication (new way) for device verification. This extra layer of security to reduces the risk of mobile fraud during critical transactions.
What data powers
Network Authentication?
How Shush silently authenticates devices using SIM and networking attributes only available from the MNO

Seamless Experience
What if banks and other companies could reduce mobile fraud by confirming that a login attempt is being made by the owner of the device?
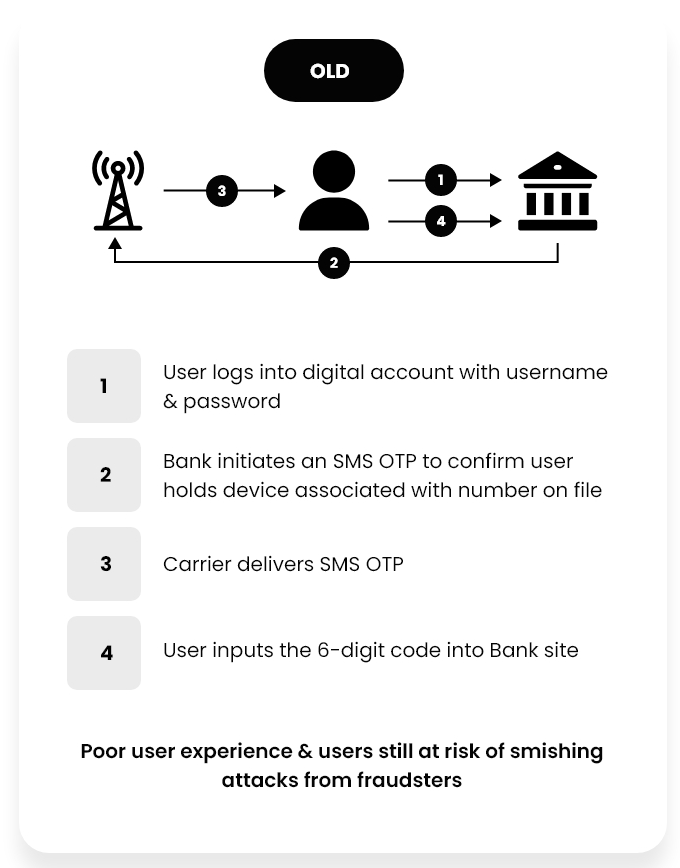
Today many mobile authentication experiences require SMS or email one-time passwords (OTPs). These are not “customer-first” experiences. Additionally, SMS was not architected as a authentication method, and the National Institute of Standards and Technology (NIST) states that “due to the risk that SMS may be intercepted or redirected,” businesses should consider alternative authentication methods.
Simply put, authentication using SMS creates friction and gives a false sense of security. Email and authenticator apps require switching apps and add to the complexity of a simple transaction.
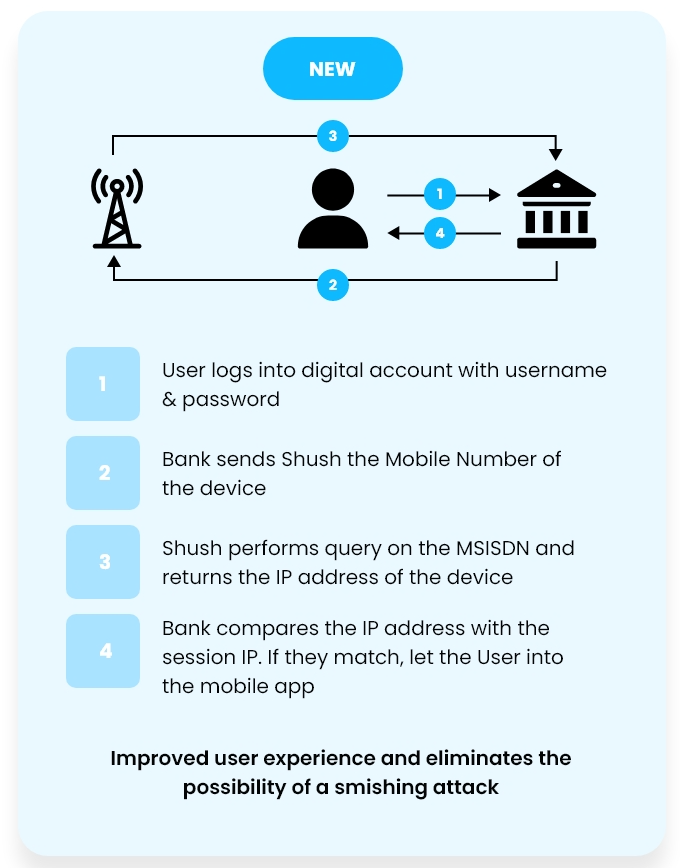
By adding Network Authentication a brand's mobile experience is leveled up without sacrificing User Experience.
Silent is Simple
Shush is partnering with mobile network operators around the globe to offer brands and users a better way to authenticate. The Shush solution uses mobile network-based technology to offer strong authentication.
When you turn on your phone, it automatically connects to your mobile network operator and authenticates your device and SIM card. As a user, you didn’t have to do anything. Shush Sherlock uses this same SIM-based authentication to confirm mobile phone number possession.
Shush Network Authentication leverages SIM data and authoritative signals across our global carrier network to instantly verify user authenticity. This blocks SIM swap attacks without any action needed by authorized users, ensuring a secure, passwordless sign-in experience.

Who are Shush Customers?

Shush works directly with the largest mobile network operators across the globe to solve the supply-side of the network authentication business. Our solution resides within the trusted and highly secure mobile operator network to allow demand side partners the ability to offer network authentication to banks and other companies.
By creating a more secure alternative to OTPs codes at the network level we provide both brands and mobile app developers a solution that requires zero updates to mobile apps. Shush works without any integration at the mobile app level.
While there many demand-side partners in the mobile ecosystem, mobile network operators need a supply-side partner to enter the network authentication market --
enter Shush Sherlock. Shush is dedicated to enabling mobile network operator with
a cloud-based supply-side solution.
Contact Us






